Notizie per Categorie
Articoli Recenti
- New whitepaper outlines the taxonomy of failure modes in AI agents 24 Aprile 2025
- Understanding the threat landscape for Kubernetes and containerized assets 23 Aprile 2025
- [Launched] Generally Available: Instance Mix for Virtual Machine Scale Sets 22 Aprile 2025
- Microsoft’s AI vision shines at MWC 2025 in Barcelona 22 Aprile 2025
- [Launched] Generally Available: Announcing the Next generation Azure Data Box Devices 22 Aprile 2025
- [Launched] Generally Available: Cross-Region Data Transfer Capability in Azure Data Box Devices 21 Aprile 2025
- [Launched] Generally Available: Azure Ultra Disk Storage is now available in Spain Central 21 Aprile 2025
- [Launched] Generally Available: Azure Firewall resource specific log tables get Azure Monitor Basic plan support 21 Aprile 2025
- Hannover Messe 2025: Microsoft puts industrial AI to work 21 Aprile 2025
- Securing our future: April 2025 progress report on Microsoft’s Secure Future Initiative 21 Aprile 2025
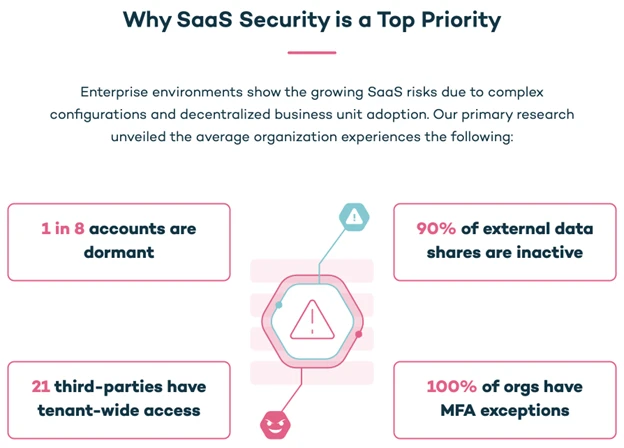
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA. Software as a service (SaaS) adoption has accelerated at a lightning speed, enabling collaboration, automation, and innovation for businesses large and small across every industry vertical—from government, education, financial service[…]
Read MoreAs the most influential technology of our lifetime, AI has the power to reshape how organizations secure their environments. AI’s impact on cybersecurity and the efforts of Microsoft to bring generative AI to organizations worldwide will be a major topic at the Microsoft Secure digital event on March[…]
Read MoreToday we are releasing an open automation framework, PyRIT (Python Risk Identification Toolkit for generative AI), to empower security professionals and machine learning engineers to proactively find risks in their generative AI systems. At Microsoft, we believe that security practices and generative AI responsibilities need to be a[…]
Read More
The process of writing, refining, and optimizing inputs—or “prompts”—to encourage generative AI systems to create specific, high-quality outputs is called prompt engineering. It helps generative AI models organize better responses to a wide range of queries—from the simple to the highly technical. The basic rule is that good[…]
Read More
The Network and Information Security Directive 2 (NIS2) is a continuation and expansion of the previous European Union (EU) cybersecurity directive introduced back in 2016. With NIS2, the EU expands the original baseline of cybersecurity risk management measures and reporting obligations to include more sectors and critical organizations.[…]
Read More
The world of cybersecurity is undergoing a massive transformation. AI is at the forefront of this change, and has the potential to empower organizations to defeat cyberattacks at machine speed, address the cyber talent shortage, and drive innovation and efficiency in cybersecurity. However, adversaries can use AI as[…]
Read MoreOver the last year, the speed, scale, and sophistication of attacks has increased alongside the rapid development and adoption of AI. Defenders are only beginning to recognize and apply the power of generative AI to shift the cybersecurity balance in their favor and keep ahead of adversaries. At[…]
Read More
Industry leading organizations across the globe are using Microsoft Power Platform to build applications, automate business processes, and drive innovation. In our recent earnings call, we highlighted that there are more than 10,000 organizations already utilizing Microsoft Copilot Studio to craft tailored copilots. With more than 230,000 organizations[…]
Read More
Organizations everywhere are on a lightning-fast learning trajectory to understand the potential of generative AI and its implications for their security, their workforce, and the industry at large. AI is quickly becoming a force multiplier—presenting significant opportunities for security teams to increase productivity, save time, upskill resources, and[…]
Read More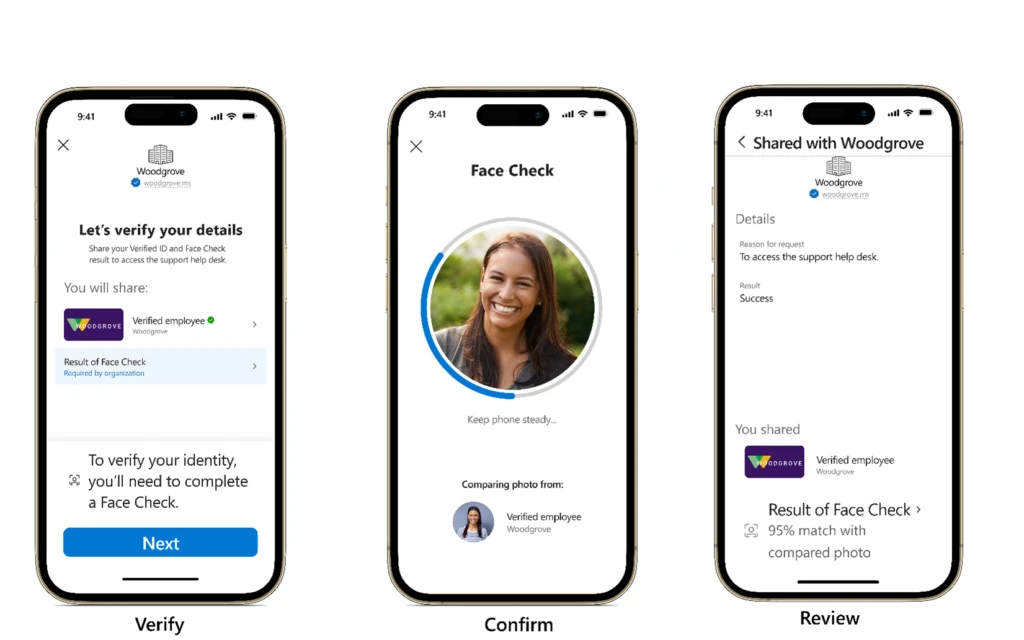
Today, I’m thrilled to announce the expansion of Microsoft Entra Verified ID to include Face Check—a privacy-respecting facial matching feature for high-assurance verifications, which is now in preview. Watch the video to learn more and read on for how you can get started today. Try Face Check for yourself.[…]
Read More