Notizie per Categorie
Articoli Recenti
- New whitepaper outlines the taxonomy of failure modes in AI agents 24 Aprile 2025
- Understanding the threat landscape for Kubernetes and containerized assets 23 Aprile 2025
- [Launched] Generally Available: Instance Mix for Virtual Machine Scale Sets 22 Aprile 2025
- Microsoft’s AI vision shines at MWC 2025 in Barcelona 22 Aprile 2025
- [Launched] Generally Available: Announcing the Next generation Azure Data Box Devices 22 Aprile 2025
- [Launched] Generally Available: Cross-Region Data Transfer Capability in Azure Data Box Devices 21 Aprile 2025
- [Launched] Generally Available: Azure Ultra Disk Storage is now available in Spain Central 21 Aprile 2025
- [Launched] Generally Available: Azure Firewall resource specific log tables get Azure Monitor Basic plan support 21 Aprile 2025
- Hannover Messe 2025: Microsoft puts industrial AI to work 21 Aprile 2025
- Securing our future: April 2025 progress report on Microsoft’s Secure Future Initiative 21 Aprile 2025
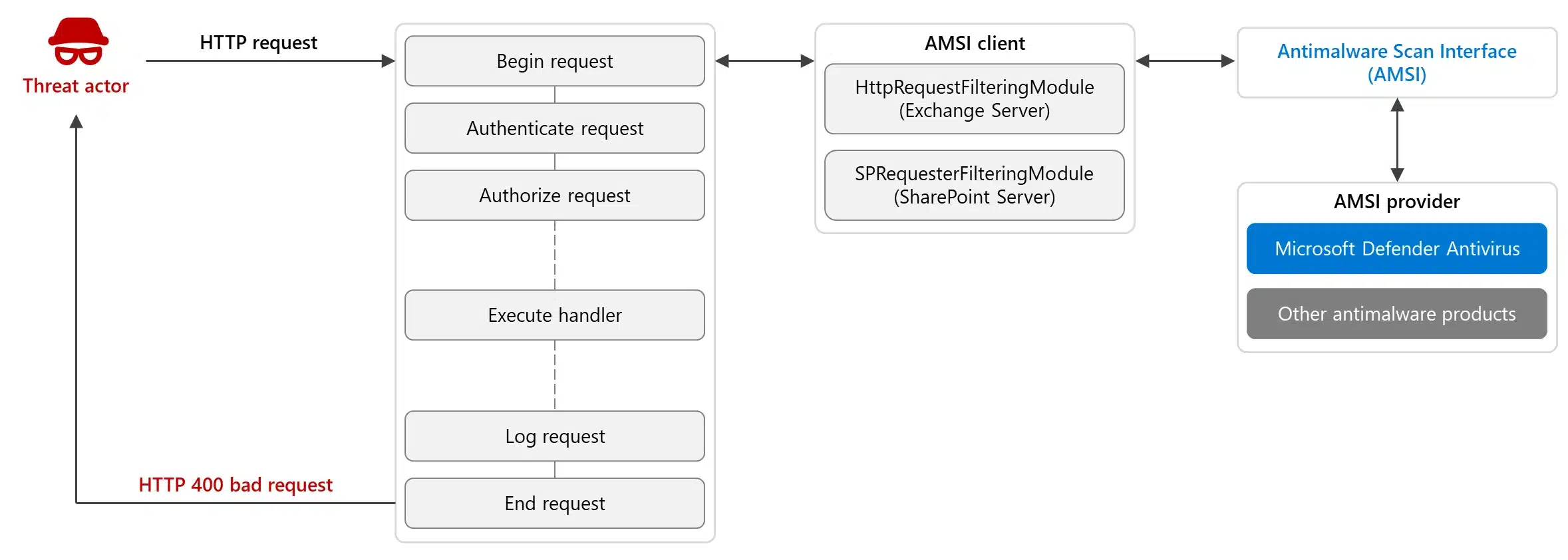
Exchange Server and SharePoint Server are business-critical assets and considered crown jewels for many organizations, making them attractive targets for attacks. To help customers protect their environments and respond to these attacks, Exchange Server and SharePoint Server now integrate with the Windows Antimalware Scan Interface (AMSI), a versatile[…]
Read More
In recent years, human-operated cyberattacks have undergone a dramatic transformation. These attacks, once characterized by sporadic and opportunistic attacks, have evolved into highly sophisticated, targeted campaigns aimed at causing maximum damage to organizations, with the average cost of a ransomware attack reaching $9.36 million in 2024.1 A key[…]
Read MoreMicrosoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC) have discovered post-compromise exploitation of a zero-day elevation of privilege vulnerability in the Windows Common Log File System (CLFS) against a small number of targets. The targets include organizations in the information technology (IT) and real estate[…]
Read More
Microsoft launched its Cybersecurity Governance Council in 2024, and with it, named a group of deputy chief information security officers that ensure comprehensive oversight of the company’s cybersecurity risk, defense, and compliance. These leaders work in tandem with product and engineering leaders across the company to create accountability[…]
Read MoreAre you looking for guidance on how to effectively integrate security best practices within your Azure and AI projects? We know the pace of technological innovation offers as many opportunities as it does challenges. However, security cannot be an afterthought as you create Azure deployments and accelerate AI[…]
Read More
As Tax Day approaches in the United States on April 15, Microsoft has observed several phishing campaigns using tax-related themes for social engineering to steal credentials and deploy malware. These campaigns notably use redirection methods such as URL shorteners and QR codes contained in malicious attachments and abuse[…]
Read More
As Tax Day approaches in the United States on April 15, Microsoft has observed several phishing campaigns using tax-related themes for social engineering to steal credentials and deploy malware. These campaigns notably use redirection methods such as URL shorteners and QR codes contained in malicious attachments and abuse[…]
Read More
As Tax Day approaches in the United States on April 15, Microsoft has observed several phishing campaigns using tax-related themes for social engineering to steal credentials and deploy malware. These campaigns notably use redirection methods such as URL shorteners and QR codes contained in malicious attachments and abuse[…]
Read More
The cyberthreat landscape is evolving at an unprecedented pace, becoming increasingly dangerous and complex. Nation-state threat actors and cybercriminals are employing advanced tactics and generative AI to execute highly sophisticated attacks. This situation is further compounded by outdated technology and systems, shortage of cybersecurity talent, and antiquated processes,[…]
Read More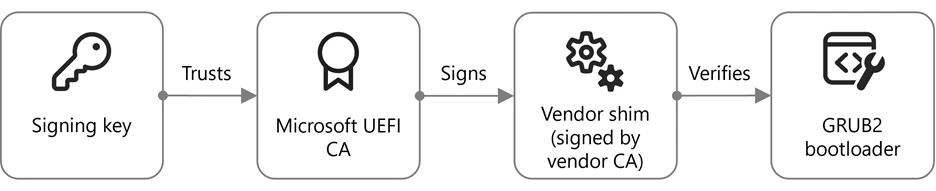
By leveraging Microsoft Security Copilot to expedite the vulnerability discovery process, Microsoft Threat Intelligence uncovered several vulnerabilities in multiple open-source bootloaders, impacting all operating systems relying on Unified Extensible Firmware Interface (UEFI) Secure Boot as well as IoT devices. The vulnerabilities found in the GRUB2 bootloader (commonly used[…]
Read More