Notizie per Categorie
Articoli Recenti
- [Launched] Generally Available: ACLs (Access Control Lists) for Local Users in Azure Blob Storage SFTP 17 Aprile 2025
- [Launched] Generally Available: New major version of Durable Functions 17 Aprile 2025
- [Launched] Generally Available: Azure SQL Trigger for Azure Functions in Consumption plan 17 Aprile 2025
- [In preview] Public Preview: Rule-based routing in Azure Container Apps 17 Aprile 2025
- [In preview] Private Preview: DCesv6 and ECesv6 series confidential VMs with Intel® TDX 17 Aprile 2025
- [Launched] Generally Available: ExpressRoute Metro Peering locations and Global Reach are now available in more regions 17 Aprile 2025
- [Launched] Generally Available: Azure Front Door custom cipher suite 17 Aprile 2025
- Microsoft’s Secure by Design journey: One year of success 17 Aprile 2025
- [In development] Private Preview: Azure Backup for AKS Now Supports Azure File Share-based Persistent Volumes 16 Aprile 2025
- [In preview] Public Preview: Remote Model Context Protocol (MCP) support in Azure Functions 16 Aprile 2025

Leading organizations worldwide are harnessing Microsoft Power Platform to revolutionize their operations, with 33 million monthly active users driving innovation and transformation. From groundbreaking applications to significant outcomes, our customer stories vividly illustrate the tangible impact of our technology. We’re thrilled to showcase some of these inspiring stories[…]
Read More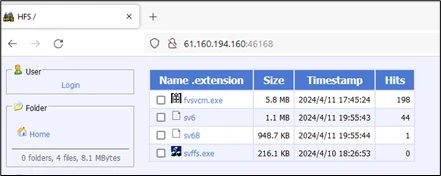
Attackers are constantly seeking new vulnerabilities to compromise Kubernetes environments. Microsoft recently uncovered an attack that exploits new critical vulnerabilities in OpenMetadata to gain access to Kubernetes workloads and leverage them for cryptomining activity. OpenMetadata is an open-source platform designed to manage metadata across various data sources. It[…]
Read More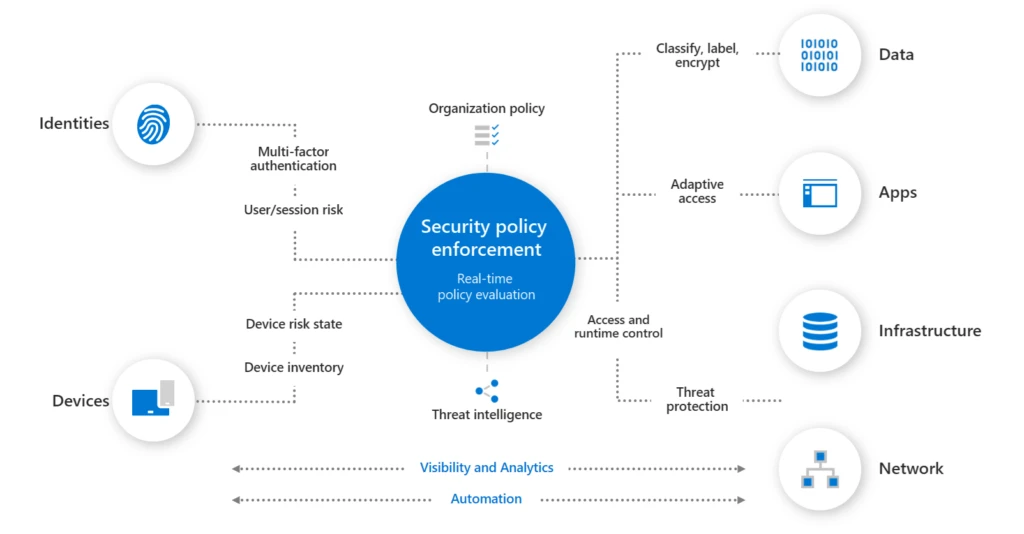
The Department of Defense (DoD) Zero Trust Strategy1 and accompanying execution roadmap2 sets a path for achieving enterprise-wide target-level Zero Trust by 2027. The roadmap lays out vendor-agnostic Zero Trust activities that DoD Components and Defense Industrial Base (DIB) partners should complete to achieve Zero Trust capabilities and[…]
Read More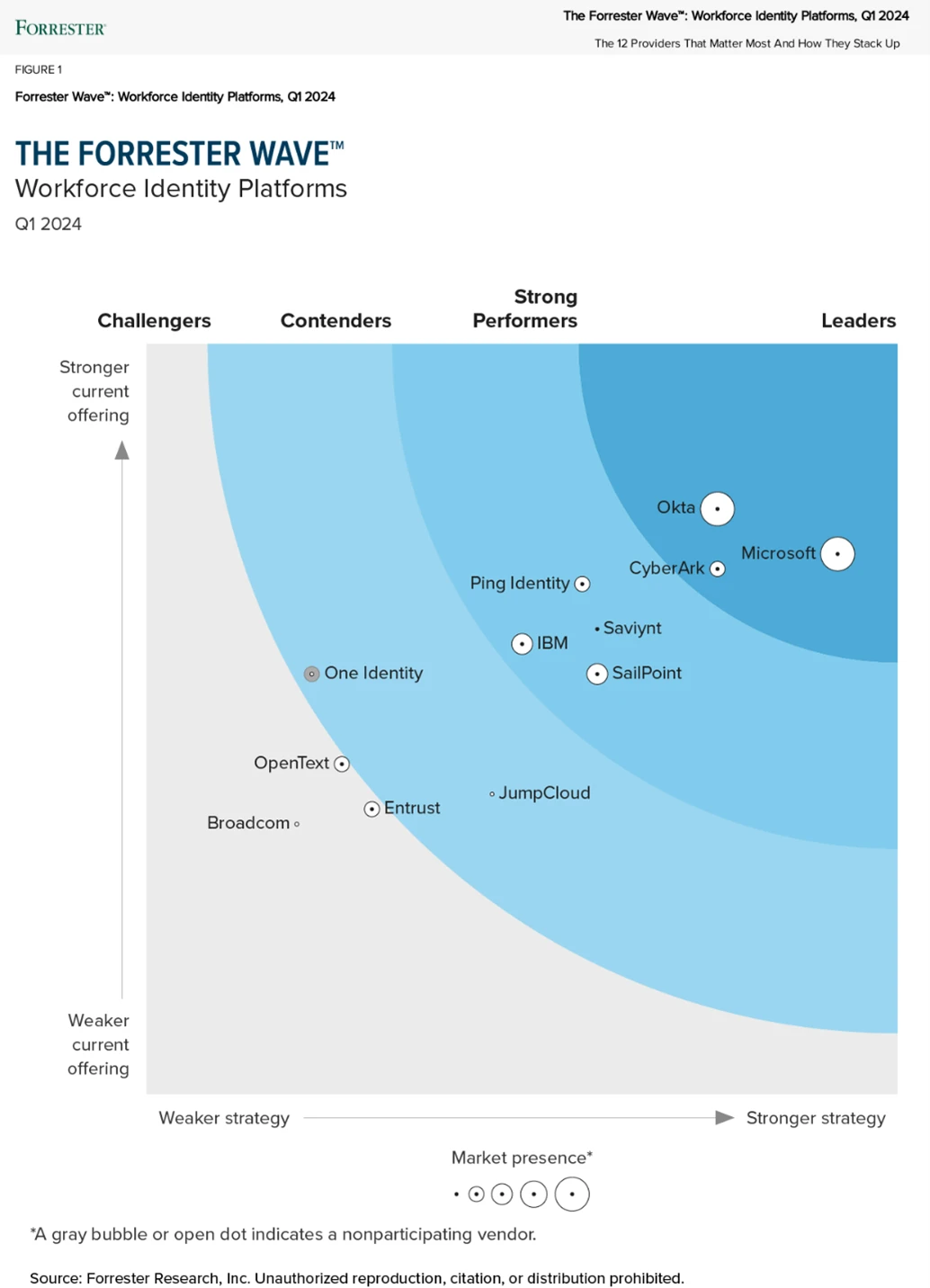
We’re thrilled to announce that Forrester has recognized Microsoft as a Leader in the Forrester Wave™: Workforce Identity Platforms, Q1 2024 report. We’re proud of this recognition, which we believe reflects our commitment to delivering advanced solutions that cater to the evolving needs of our customers in the[…]
Read More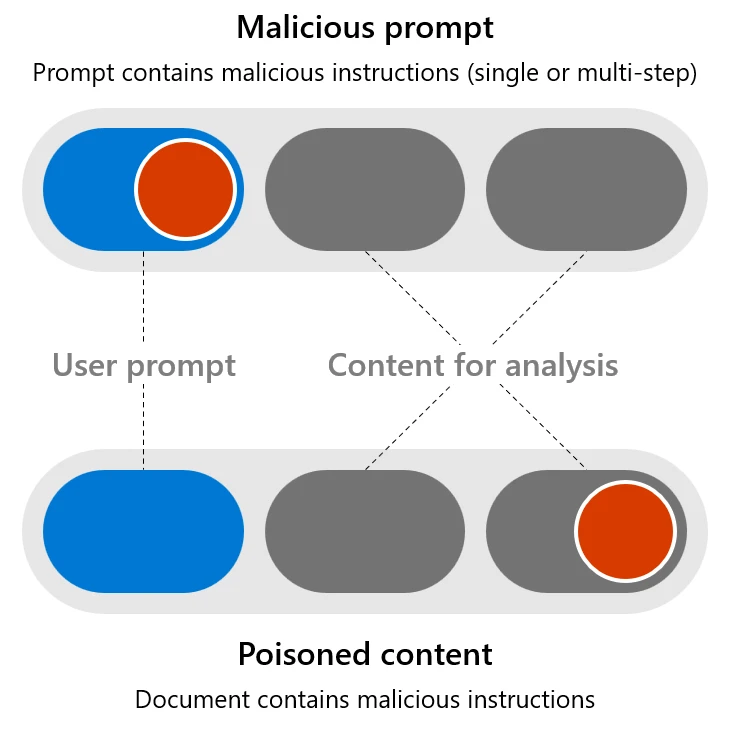
As we continue to integrate generative AI into our daily lives, it’s important to understand the potential harms that can arise from its use. Our ongoing commitment to advance safe, secure, and trustworthy AI includes transparency about the capabilities and limitations of large language models (LLMs). We prioritize[…]
Read More
Today we launched the 2024 release wave 1 for Microsoft Dynamics 365 and Microsoft Power Platform, a rollout of new features and enhanced capabilities slated for release between April and September 2024. These updates include new Microsoft Copilot capabilities across Dynamics 365 and Microsoft Power Platform—as well as role-based extensions of Copilot[…]
Read More
The security of your organization directly correlates with your ability to transform and achieve your business objectives. Microsoft can help you make that happen, with our powerful combination of large-scale data and threat intelligence, end-to-end protection, and responsible AI. Recently at Microsoft Secure, we shared our latest innovations[…]
Read More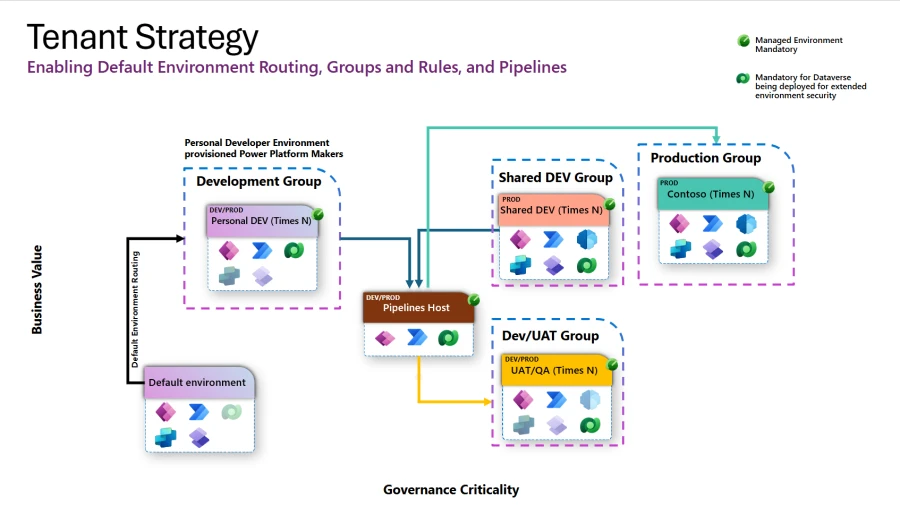
Preview Microsoft Power Platform environment groups and rules As organizations expand their Microsoft Power Platform footprint to meet the needs of their users for application modernization and the inclusion of Microsoft Copilot, administrators can utilize premium features such as managed environments to govern at-scale quickly and easily, while[…]
Read More
Today, I am excited to announce the public preview of our unified security operations platform. When we announced a limited preview in November 2023, it was one of the first security operations center platforms that brought together the full capabilities of an industry-leading cloud-native security information and event[…]
Read More
We know managing privacy is harder than ever. The increasing complexity of regulatory requirements and constantly changing regulations make day-to-day privacy management a challenge. Manual, inefficient processes and inflexible tools can make it difficult for organizations to know where data is located and how it’s being used. The[…]
Read More