Notizie per Categorie
Articoli Recenti
- Retirement: Canonical Ubuntu 20.04 LTS Reaching End of Standard Support on May 31, 2025 9 Aprile 2025
- Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI 9 Aprile 2025
- [In preview] Public Preview: Power BI Connector for vCore-based Azure Cosmos DB for MongoDB 9 Aprile 2025
- [In preview] Public Preview: Fabric Mirroring for Azure Database for PostgreSQL – flexible server 9 Aprile 2025
- [Launched] Generally Available: Azure SQL Updates for Early-April 2025 9 Aprile 2025
- [Launched] Generally Available: I/O Performance Analysis—SQL Server on Azure Virtual Machines 9 Aprile 2025
- [In preview] Public Preview: Self-serve enablement for all versions and deletes mode in Azure Cosmos DB for NoSQL 9 Aprile 2025
- How cyberattackers exploit domain controllers using ransomware 9 Aprile 2025
- [In preview] Public Preview: New Enhancements to Carbon Optimization – Expanded API limits, Subscription Reader Access, and Filtering Options 8 Aprile 2025
- Exploitation of CLFS zero-day leads to ransomware activity 8 Aprile 2025
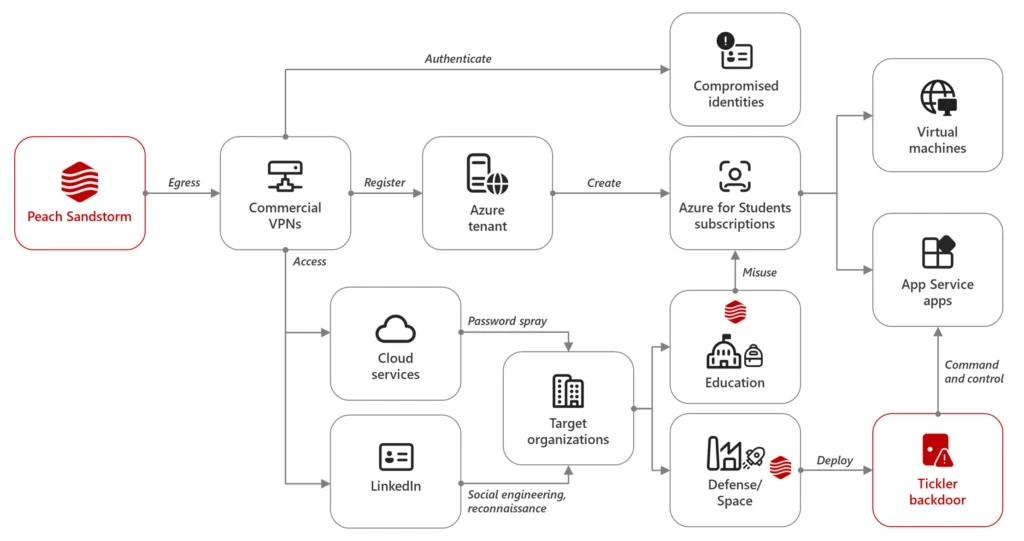
Between April and July 2024, Microsoft observed Iranian state-sponsored threat actor Peach Sandstorm deploying a new custom multi-stage backdoor, which we named Tickler. Tickler has been used in attacks against targets in the satellite, communications equipment, oil and gas, as well as federal and state government sectors in[…]
Read More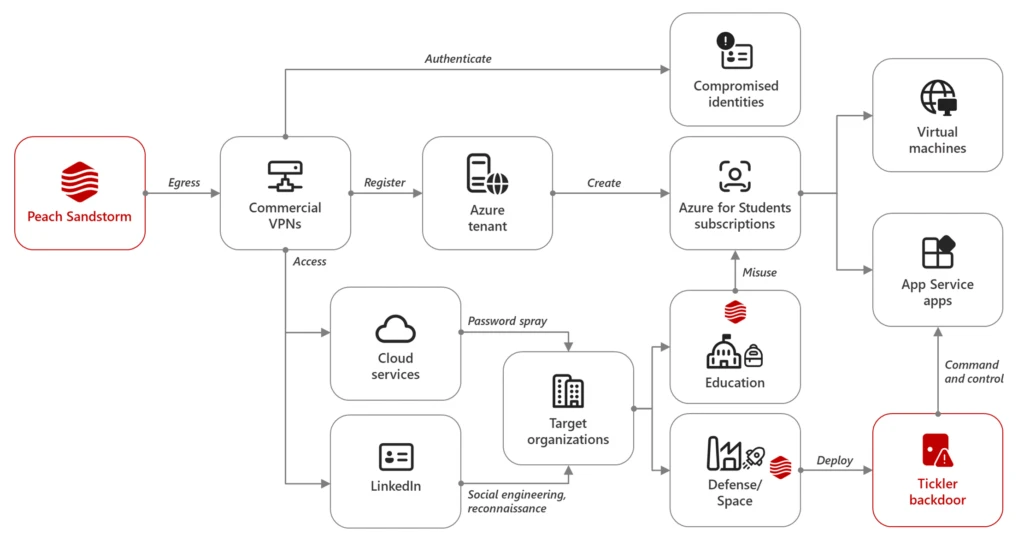
Between April and July 2024, Microsoft observed Iranian state-sponsored threat actor Peach Sandstorm deploying a new custom multi-stage backdoor, which we named Tickler. Tickler has been used in attacks against targets in the satellite, communications equipment, oil and gas, as well as federal and state government sectors in[…]
Read More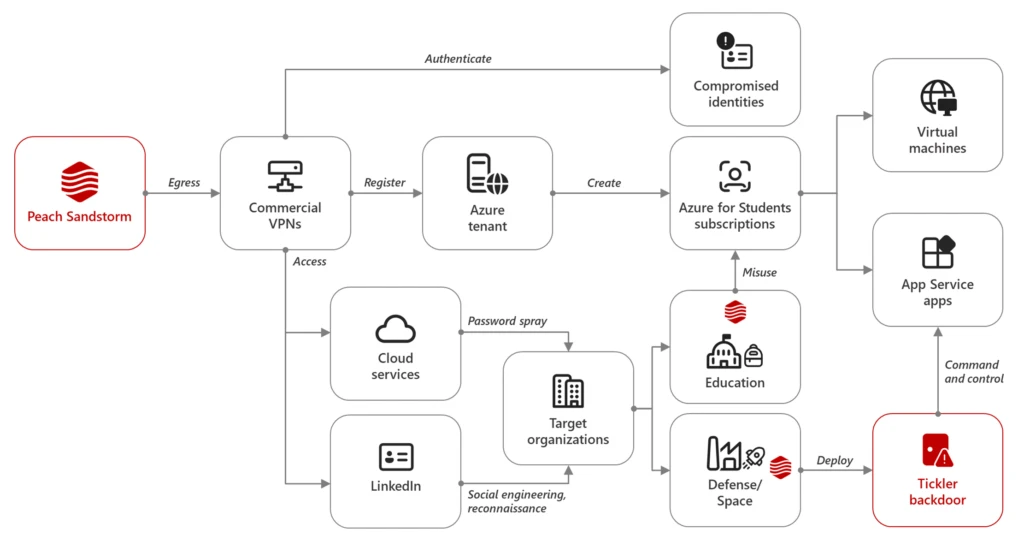
Between April and July 2024, Microsoft observed Iranian state-sponsored threat actor Peach Sandstorm deploying a new custom multi-stage backdoor, which we named Tickler. Tickler has been used in attacks against targets in the satellite, communications equipment, oil and gas, as well as federal and state government sectors in[…]
Read More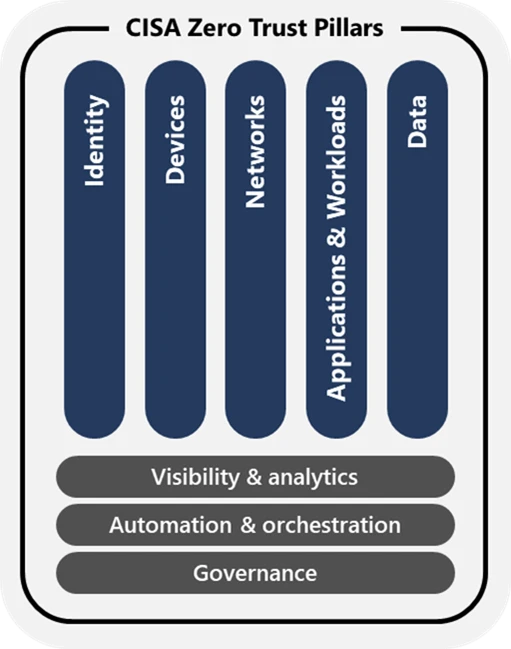
If you’re in charge of cybersecurity for a United States government agency, you’re already familiar with Memorandum M-22-09, “Moving the U.S. Government Toward Zero Trust Cybersecurity Principles,” which the US Office of Management and Budget issued in January 2022. This memo set a September 30, 2024, deadline for[…]
Read More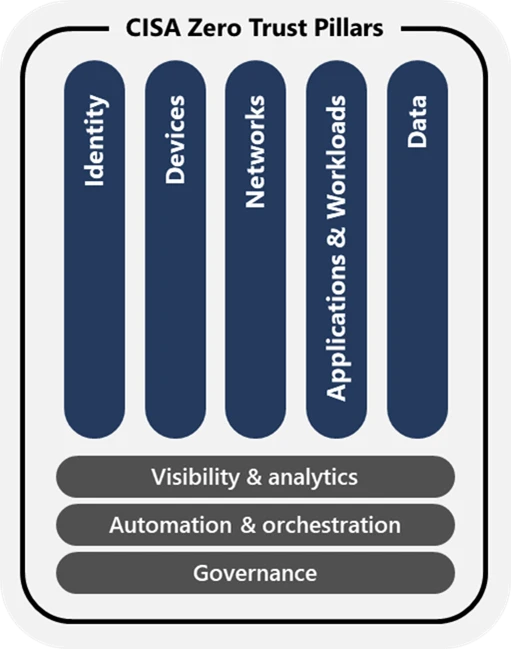
If you’re in charge of cybersecurity for a United States government agency, you’re already familiar with Memorandum M-22-09, “Moving the U.S. Government Toward Zero Trust Cybersecurity Principles,” which the US Office of Management and Budget issued in January 2022. This memo set a September 30, 2024, deadline for[…]
Read More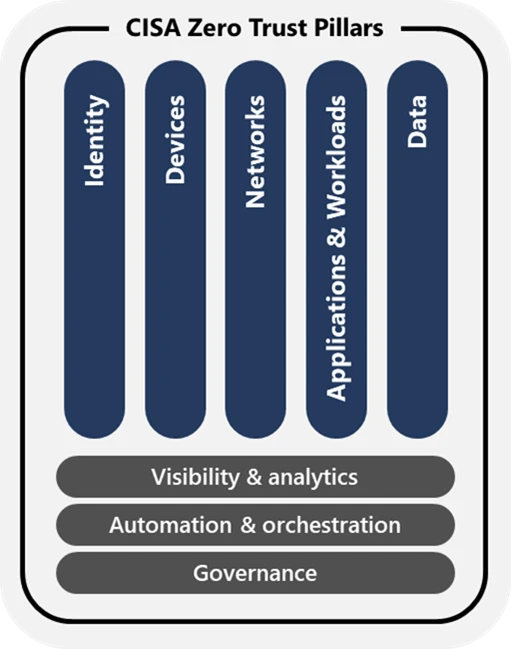
If you’re in charge of cybersecurity for a United States government agency, you’re already familiar with Memorandum M-22-09, “Moving the U.S. Government Toward Zero Trust Cybersecurity Principles,” which the US Office of Management and Budget issued in January 2022. This memo set a September 30, 2024, deadline for[…]
Read More
For the second year, the Microsoft AI Tour will bring together security practitioners, developers, and other technology professionals to learn about the latest AI innovations across the full Microsoft Security stack in multiple cities around the globe. Whether you’re a decision maker who evaluates investments, an IT team[…]
Read More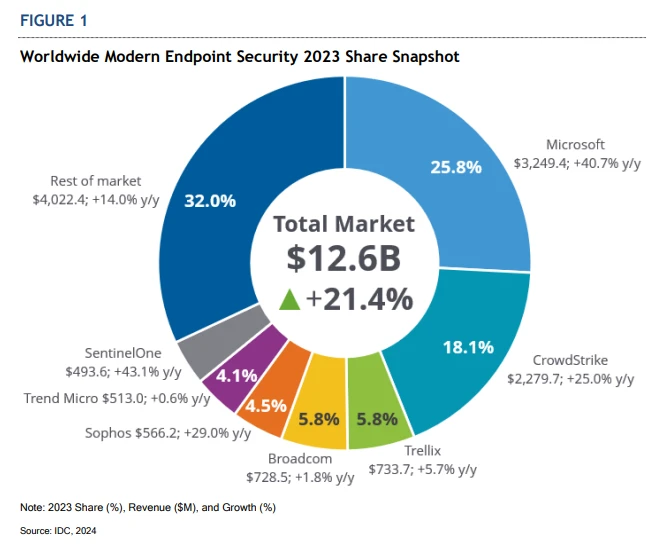
Today’s remote workforce has become the standard. But the security challenges created by remote work continue to be a key point of exploitation by bad actors. In fact, 80% to 90% of all successful ransomware compromises originate through unmanaged devices.1 Because endpoints are a broadly targeted vector and[…]
Read More
Get ready to ignite your passion for innovation at the 2024 Power Platform Community Conference (PPCC). This year, we’re bringing together some of the brightest minds and most enthusiastic members of the Microsoft Power Platform community for an unforgettable experience. Whether you’re a seasoned professional or just starting[…]
Read More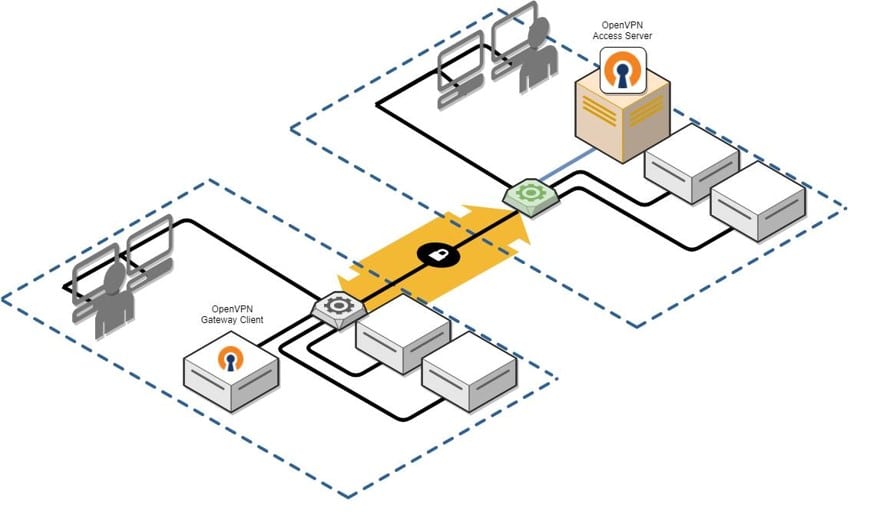
Microsoft researchers recently identified multiple medium severity vulnerabilities in OpenVPN, an open-source project with binaries integrated into routers, firmware, PCs, mobile devices, and many other smart devices worldwide, numbering in the millions. Attackers could chain and remotely exploit some of the discovered vulnerabilities to achieve an attack chain[…]
Read More