Notizie per Categorie
Articoli Recenti
- Explore practical best practices to secure your data with Microsoft Purview 25 Aprile 2025
- New whitepaper outlines the taxonomy of failure modes in AI agents 24 Aprile 2025
- Understanding the threat landscape for Kubernetes and containerized assets 23 Aprile 2025
- [Launched] Generally Available: Instance Mix for Virtual Machine Scale Sets 22 Aprile 2025
- Microsoft’s AI vision shines at MWC 2025 in Barcelona 22 Aprile 2025
- [Launched] Generally Available: Announcing the Next generation Azure Data Box Devices 22 Aprile 2025
- [Launched] Generally Available: Cross-Region Data Transfer Capability in Azure Data Box Devices 21 Aprile 2025
- [Launched] Generally Available: Azure Ultra Disk Storage is now available in Spain Central 21 Aprile 2025
- [Launched] Generally Available: Azure Firewall resource specific log tables get Azure Monitor Basic plan support 21 Aprile 2025
- Hannover Messe 2025: Microsoft puts industrial AI to work 21 Aprile 2025
Microsoft Defender Experts for XDR recognized in the latest MITRE Engenuity ATT&CK® Evaluation for Managed Services
Microsoft Defender Experts for XDR demonstrated excellent managed extended detection and response (MXDR) by unifying our human-driven services and Microsoft Defender XDR in the MITRE Engenuity ATT&CK® Evaluations: Managed Services menuPass + ALPHV BlackCat.
Defender Experts for XDR offers a range of capabilities:
- Managed detection and response: Let our expert analysts manage your Microsoft Defender XDR incident queue and handle triage, investigation, and response on your behalf.
- Proactive threat hunting: Extend your team’s threat hunting capabilities and prioritize significant threats with Defender Experts for Hunting built in.
- Live dashboards and reports: Get a transparent view of our operations conducted on your behalf, along with a noise-free, actionable view of prioritized incidents and detailed analytics.
- Proactive check-ins: Benefit from remote, periodic check-ins with your named service delivery manager (SDM) team to guide your MXDR experience and improve your security posture.
- Fast and seamless onboarding: Get a guided baselining experience to ensure your Microsoft security products are correctly configured.
Microsoft Defender Experts for XDR
Give your security operations center (SOC) team coverage with leading end-to-end protection and expertise.
Cyberattacks detected by Defender Experts for XDR
In the first cyberattack, Defender Experts for XDR provided detection, visibility, and coverage under what Microsoft Threat Intelligence tracks as the threat actor Purple Typhoon. From the early steps in the intrusion, our team alerted the customer that 11 systems and 13 accounts were compromised via a malicious Remote Desktop Protocol (RDP) session, leveraging a Dynamic Link Library (DLL) Search Order Hijacking on a legitimate Notepad++ executable. As is common with this threat actor, the next cyberattack, established a Quasar RAT backdoor triggering keylogging, capturing credentials for the domain admin. After the loaders were executed, scheduled tasks were used to move laterally, execute discovery commands on internal network areas, and complete credential theft dumping.
For the second cyberattack, which used BlackCat ransomware, Defender Experts for XDR detected and provided extensive guidance on investigation and remediation actions. The BlackCat ransomware, also known as ALPHV, is a prevalent cyberthreat and a prime example of the growing ransomware-as-a-service (RaaS) gig economy. It’s noteworthy due to its unconventional programming language (Rust), multiple target devices and possible entry points, and affiliation with prolific threat activity groups. While BlackCat’s arrival and execution vary based on the actors deploying it, the outcome is the same—target data is encrypted, exfiltrated, and used for “double extortion,” where attackers threaten to release the stolen data to the public if the ransom isn’t paid. This attack used access broker credentials to perform lateral movement, exfiltrate sensitive data via privileged execution, and execute ransomware encryption malware.
In both cyberattacks, our team focused on providing focused email, in-product focus to guide the customer, and in a real world cyberattack, our service and product would take disruption actions to stop the cyberattack.
Comprehensive threat hunting, managed response, and product detections
With complex cyberattacks, security operations teams need robust guidance on what is happening and how to prioritize remediation efforts. Throughout this evaluation, we provided over 18 incidents, 196 alerts, and enriched product detections with human-driven guidance via email and in product experiences using Managed responses. This includes a detailed investigation summary, indicators of compromise (IOCs), advanced hunting queries (AHQs), and prioritized remediation actions to help contain the cyberthreat. Our world class hunting team focuses on providing initial response to a cyberattack, then iterations on updates based on new threat intelligence findings and other enrichment.
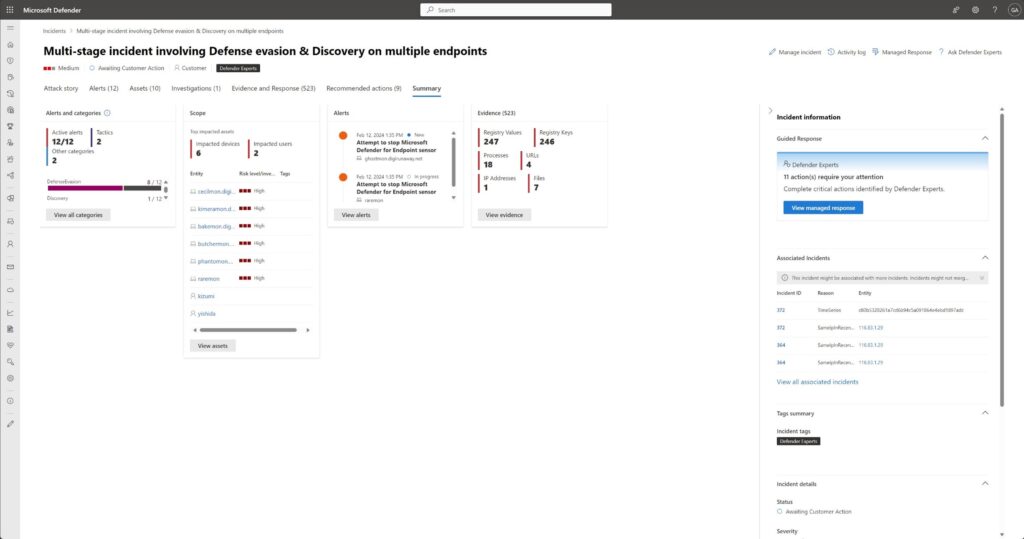
Figure 1. The incident and alerts are tagged with Defender Experts and detailed analysis provided under view Managed response.

Figure 2. Managed response showing details of investigation summary, IOCs, and TTPs.
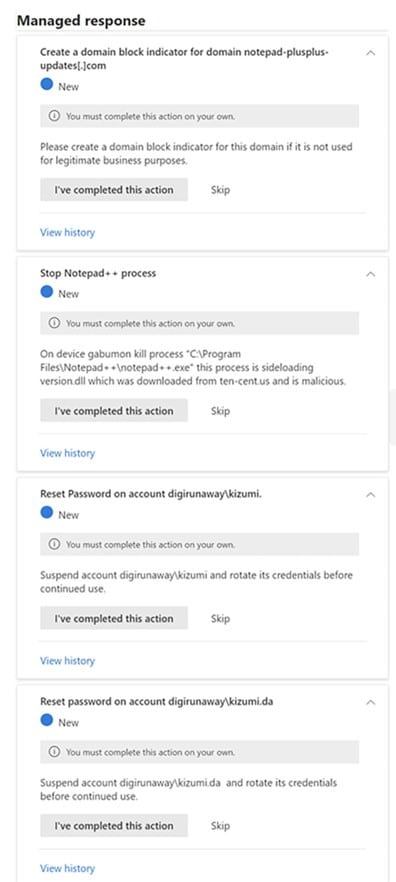
Figure 3. Managed response focused remediation one-click actions such as blocking indicator, stopping a malicious process, and resetting passwords.
AI-driven attack disruption with Microsoft Defender XDR
As the second cyberattack leveraged BlackCat ransomware, Microsoft Defender XDR’s attack disruption capability automatically contained the threat and then followed up with hunter guidance on additional containment. This capability combines our industry-leading detection with AI-powered enforcement mechanisms to help mitigate cyberthreats early on in the cyberattack chain and contain their advancement. Analysts have a powerful tool against human-operated cyberattacks while leaving them in complete control of investigating, remediating, and bringing assets back online.
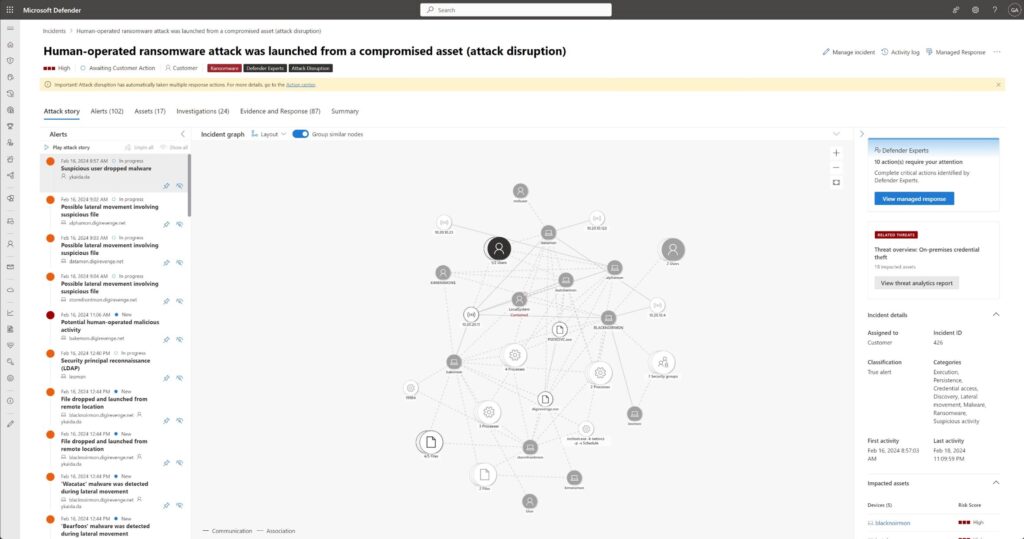
Figure 4. A summary attack graph, managed responses and attack disruption automatically handling this ransomware threat.
Seamless alert prioritization and consolidation into notifications for the SOC
We provide prioritization and focus for a typical customer’s SOC team using tags and incident titles with Defender Experts where we enrich product detections. In addition, a dedicated SDM will conduct periodic touchpoints with customers to share productivity and service metrics, provide insights on any vulnerabilities or changes in their environment, solicit feedback, and make best practices recommendations. Our customers see a reduction in total incident volume over time, improvements in security posture, and overall lower operational overhead. Learn how Defender Experts helps Westminster School.

Figure 5. Summary of all incidents and Defender Experts tag to help filter and prioritize for customers.
Commitment to Microsoft MXDR partners
We continue our commitment to support our partners in our Microsoft-verified MXDR program. We know that a single provider can’t meet the unique needs of every organization, so we frequently collaborate with our ecosystem of partners to provide customers the flexibility to choose what works best for them—and to leverage those trusted relationships for the best outcomes and returns on their investment.
We acknowledge that there are areas for discussion and enhancement, but we will take these as a valuable learning opportunity to continuously improve our products and services for the customers we serve. We appreciate our ongoing collaboration with MITRE as the managed services evaluation process evolves with the growing cyberthreat landscape. We thank MITRE Engenuity for the opportunity to contribute to and participate in this year’s evaluation.
Learn more about Microsoft Defender Experts for XDR
To learn more, visit the Microsoft Defender Experts for XDR web page, read the Defender Experts for XDR docs page, and subscribe to our ongoing news at the Microsoft Security Experts blog.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.
© June 2024. The MITRE Corporation. This work is reproduced and distributed with the permission of The MITRE Corporation.
The post Microsoft Defender Experts for XDR recognized in the latest MITRE Engenuity ATT&CK® Evaluation for Managed Services appeared first on Microsoft Security Blog.
Source: Microsoft Security
