Notizie per Categorie
Articoli Recenti
- [In preview] Public Preview: Azure Blob-to-Blob migration made simple with Azure Storage Mover 18 Dicembre 2025
- AI transformation in financial services: 5 predictors for success in 2026 18 Dicembre 2025
- New Microsoft e-book: 3 reasons point solutions are holding you back 18 Dicembre 2025
- [In preview] Public Preview: Service Bus SDK type bindings in Azure Functions for Node.js 17 Dicembre 2025
- [Launched] Generally Avaailable: Azure SQL updates for early December 2025 17 Dicembre 2025
- [In preview] Public Preview: Use Azure SRE Agent with Azure Cosmos DB 17 Dicembre 2025
- Access Fabric: A modern approach to identity and network access 17 Dicembre 2025
- [In preview] Generally Available: Azure NetApp Files cross-zone-region replication (CZRR) 16 Dicembre 2025
- [In preview] Public Preview: Azure NetApp Files advanced ransomware protection 16 Dicembre 2025
- Defending against the CVE-2025-55182 (React2Shell) vulnerability in React Server Components 15 Dicembre 2025
Microsoft Incident Response tips for managing a mass password reset
Explore how effective incident response helps organizations detect, address, and stop cyberattacks
As part of any robust incident response plan, organizations often work through potential security weaknesses by responding to hypothetical cyberthreats. In this blog post, we’ll imagine a scenario in which a threat actor uses malware to infect the network, moving laterally throughout the environment and attempting to escalate their admin rights along the way. In this hypothetical scenario, we’ll assume containment of the incident requires a mass password reset.
Despite technological advances, many organizations still depend heavily on passwords, making them vulnerable to cyberthreats. During a ransomware attack, the need for mass password resets becomes urgent. Unfortunately, admins can quickly become overwhelmed, burdened with the daunting task of resetting passwords for countless users across multiple connected devices. The surge in help desk calls and service tickets as users face authentication issues on multiple fronts can significantly disrupt business operations. But it’s imperative to secure all digital access points to swiftly mitigate risks and restore system integrity. So how do we manage a mass password reset while minimizing disruption to users and the business?
This blog post delves into the processes and technologies involved in managing a mass password reset, in alignment with expert advice from Microsoft Incident Response. We’ll explore the necessity of mass password resets and the specific methods and security measures that Microsoft recommends to effectively safeguard identities. For a more technical explanation, read our Tech Community post.
Surge in password-based cyberattacks
According to the most recent Microsoft Digital Defense Report, password-based attacks in 2023 increased tenfold over the previous year, with Microsoft blocking about 4,000 attacks per second through Microsoft Entra.1 This alarming rise underscores the vulnerability of password-dependent security systems. Despite this, too many companies haven’t adopted multifactor authentication, leaving them vulnerable to a variety of cyberattacks, such as phishing, credential stuffing, and brute force attacks. This makes a mass password reset not just a precaution, but a necessity in certain situations.
Deciding on a mass password reset
When the Microsoft Incident Response team determines a threat actor has had extensive access to a customer’s identity plane, a mass password reset may be the best option to restore environment security and prevent unauthorized access. Here are a few of the first questions we ask:
- When should you perform a mass password reset?
- What challenges might you face during the process?
- How should you prepare for it?
Microsoft Incident Response
Dedicated experts work with you before, during, and after a cybersecurity incident.
How to manage a mass password reset effectively
In today’s world, many of us are working from anywhere, blending home and office environments. This diversity makes executing a mass password reset particularly challenging, and the decision isn’t always clear. Organizations need to weigh the risk to the business from ransomware and down time against the disruption to users and the often overwhelming strain on IT staff. Here are the two main drivers of mass password resets, as well as advanced security measures a cybersecurity team can apply.
User-driven resets
In environments where identities sync through Microsoft Entra, there’s no need for a direct office connection to reset passwords. Using Microsoft Entra ID capabilities allows users to change their credentials at their next login. Opting for Microsoft Entra ID can also add layers of security through features like Conditional Access, making the reset process both secure and user-friendly. Conditional Access policies work by evaluating the context of each sign-in attempt and allowing you to configure requirements based on that context—like requiring users to complete multifactor authentication challenges if they’re accessing files from outside the corporate network, for example. Conditional Access policies can significantly enhance security by preventing unauthorized access during the reset process.
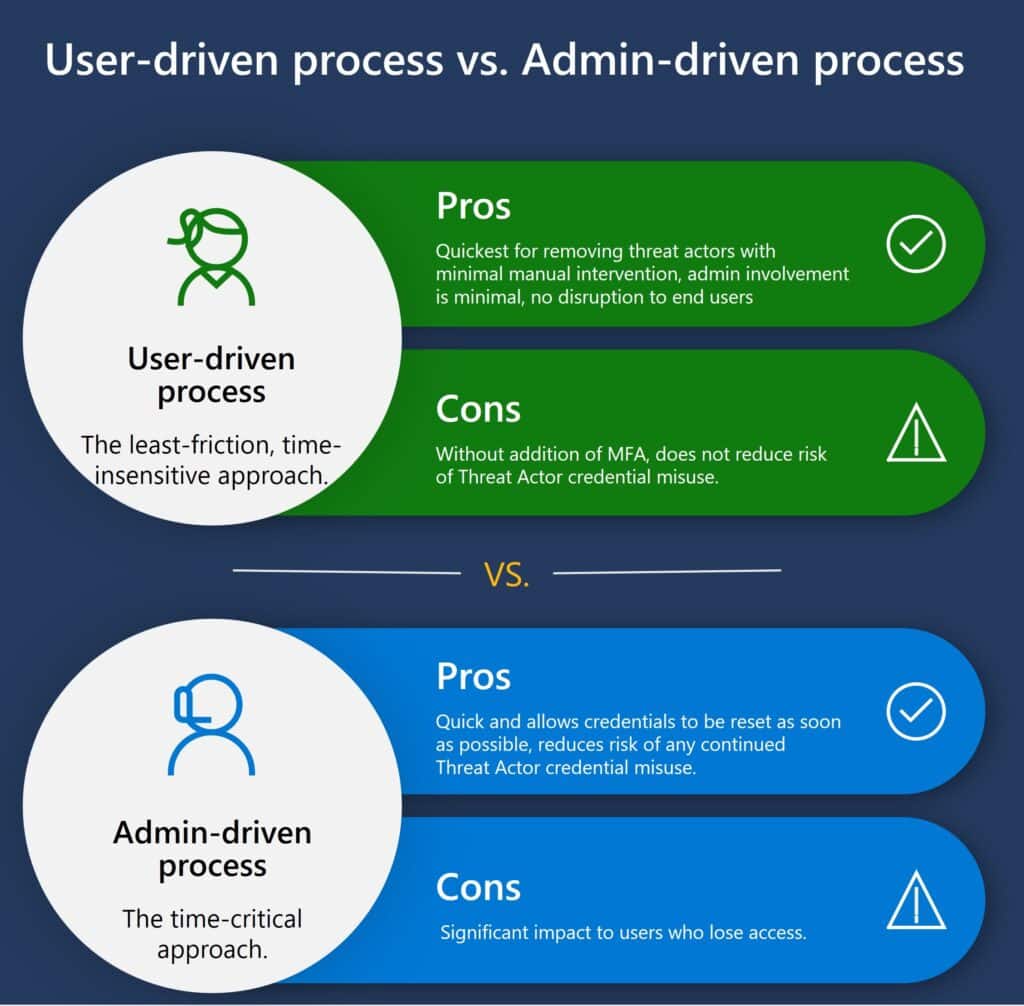
Administrator-driven resets
This method is crucial when immediate action is needed. Resetting all credentials quickly might disrupt user access, but it’s sometimes necessary to secure the system. Providing options like self-service password reset (SSPR) can help users regain access without delay. SSPR allows users to authenticate using alternative methods such as personal email addresses, phone numbers, or security questions—options available when they have been previously configured. This method not only restores access quickly but also reduces the load on help desk and support hotline departments during critical recovery phases.
Advanced security measures: Beyond basic resets
In addition to the primary reset methods, advanced security measures should be considered to enhance the security posture further. For highly privileged accounts, using privileged identity management (PIM) can manage just-in-time access, reducing the risk of exposure. PIM enables granular control over privileged accounts, allowing administrators to activate them only when necessary, which minimizes the opportunity for attackers to exploit these high-level credentials. To explore more scenarios where mass password reset might be the best option, read through our technical post.
Securing emergency access: Don’t forget to monitor
For critical accounts, manually resetting credentials ensures tighter security. It’s essential to equip emergency access accounts with phishing-resistant authentication, such as FIDO2 security keys and support from the Microsoft Authenticator app. Monitoring the activities from these accounts is crucial to ensure they are used correctly and only in emergencies. IT admins can leverage Microsoft Entra ID logs to keep a close watch on login patterns and activities, viewing real-time alerts and ensuring quick response to any suspicious actions.
Passwordless authentication and enhancing incident response
Plan a passwordless authentication deployment in Microsoft Entra ID
As cybersecurity evolves, the move toward passwordless authentication is becoming integral to enhancing incident response strategies. Traditional passwords—often vulnerable to breaches—are giving way to more secure methods like Windows Hello for Business, Microsoft Authenticator, and FIDO2 security keys. These technologies leverage biometrics and secure tokens, reducing common attack vectors such as password theft and phishing, and thereby streamlining the incident response process. Policies like a Temporary Access Pass can be configured to empower a move towards passwordless authentication, making it easier for users to register new strong authentication methods.
Implementing multifactor authentication also further strengthens security frameworks. Multifactor authentication is an essential component of basic security hygiene that can prevent 99% of account compromise attacks.1 When integrated with phishing-resistant authentication methods, together they form a formidable barrier against unauthorized access. This dual approach not only speeds up the response during security incidents but also reduces potential entry points for attackers. This transformative phase in cybersecurity shifts focus on reactive to proactive security measures, promising a future where digital safety is inherent and user interactions are inherently secure. An option to enable phish-resistant authentication is the newly released ability to use passkeys with the Microsoft Authenticator.
A mass password reset is just one of the many tools organizations need to understand and consider as part of their robust incident response plan. For a more in-depth look at scenarios that may require mass password reset, read our technical post.
Learn more
Learn more about Microsoft Incident Response and Microsoft Entra.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us on LinkedIn (Microsoft Security) and X (@MSFTSecurity) for the latest news and updates on cybersecurity.
1Microsoft Digital Defense Report 2023.
The post Microsoft Incident Response tips for managing a mass password reset appeared first on Microsoft Security Blog.
Source: Microsoft Security
