Notizie per Categorie
Articoli Recenti
- Explore practical best practices to secure your data with Microsoft Purview 25 Aprile 2025
- New whitepaper outlines the taxonomy of failure modes in AI agents 24 Aprile 2025
- Understanding the threat landscape for Kubernetes and containerized assets 23 Aprile 2025
- [Launched] Generally Available: Instance Mix for Virtual Machine Scale Sets 22 Aprile 2025
- Microsoft’s AI vision shines at MWC 2025 in Barcelona 22 Aprile 2025
- [Launched] Generally Available: Announcing the Next generation Azure Data Box Devices 22 Aprile 2025
- [Launched] Generally Available: Cross-Region Data Transfer Capability in Azure Data Box Devices 21 Aprile 2025
- [Launched] Generally Available: Azure Ultra Disk Storage is now available in Spain Central 21 Aprile 2025
- [Launched] Generally Available: Azure Firewall resource specific log tables get Azure Monitor Basic plan support 21 Aprile 2025
- Hannover Messe 2025: Microsoft puts industrial AI to work 21 Aprile 2025
Implementing Zero Trust access to business data on BYOD with Trustd MTD and Microsoft Entra
This blog post is part of the Microsoft Intelligent Security Association guest blog series. Learn more about MISA.
As more employees work remotely on a variety of devices and networks, businesses need a security model that supports this new operational efficiency. An expanding perimeter poses challenges for organizational security, exposing your company to risks from malware and data breaches from IT devices that are unknown and unsafe.
To adapt to the realities of modern work, the principles of Zero Trust have been rapidly adopted as a security best practice by businesses and security professionals alike.
A pillar of the Zero Trust framework is based on assuming devices are breached until they are explicitly verified as trusted.
This applies particularly to mobile devices, as employee-held smartphones are increasingly infected with malware, targeted by phishing attacks, or exploited due to vulnerable software and configuration. These threats on untrusted devices that access company data result in businesses suffering from cyberattacks and data breaches. By embracing the principles of Zero Trust, businesses can better manage these risks and secure themselves against mobile-borne threats by ensuring that only trusted devices have access to company data.
How Microsoft and Traced work together to ensure endpoint protection based on Zero Trust principles
United Kingdom-based cybersecurity vendor Traced Mobile Security joined the Microsoft Intelligence Security Association (MISA) with the goal of transforming Zero Trust access to business data on mobile devices.
At Traced, our vision is to live in a world where anyone can comfortably, easily, and securely use the same mobile device for work and play. MISA has helped us to do with their valuable advice, access to technical experts, and sharing our vision for safer devices.
Benedict Jones, Co-Founder, Traced
Trust nothing, verify everything.
With ever-more mobile devices accessing company networks, information, and cloud apps, customers need to be able to automatically control access to cloud apps based on the security status of a smartphone or tablet—whether it’s personal- or corporate-owned.
So Traced developed Trustd MTD to provide simple, fast, and robust Zero Trust access to those Cloud Apps for Microsoft customers. Trustd’s integration with Microsoft Azure Active Directory (Azure AD), part of the Microsoft Entra product family, helps customers achieve compliance and mitigate the growing business risks of cyberattacks and data breaches originating from company and personal mobile devices.
This means that customers can:
- Reduce the risk of data breaches, fines, and damages from cyberthreats such as Man-in-the-Middle attacks, malware, and phishing.
- Enable secure remote working without compromising efficiency.
- Automatically allow access to company data when a user’s device is validated as trusted and restrict access if it becomes untrusted.
- Protect their private data on mobile devices across most locations and networks.
“As mobile threats abound in greater numbers, we’re seeing many businesses struggling to protect themselves. We’re using Trustd MTD to enforce the principles of Zero Trust for our customers and ensure that untrusted and compromised mobile devices cannot access company data.”
Fayyaz Shah, Chief Operating Officer, METCLOUD
Through Trustd MTD’s integration with Azure AD conditional access policies, customers can automatically restrict access to thousands of Azure AD Gallery apps from users with compromised or untrusted mobile devices.
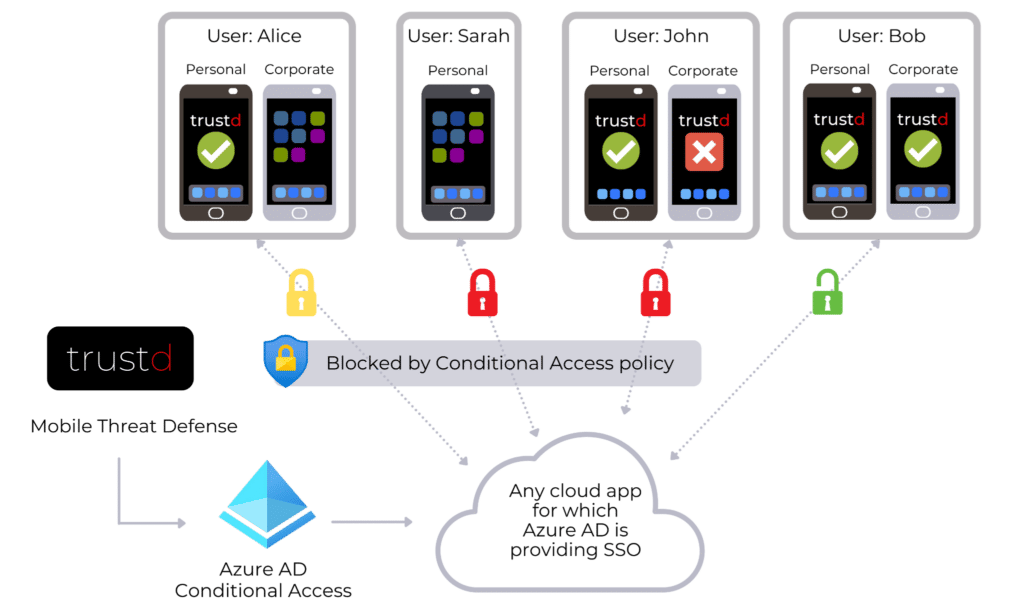
With Azure AD Single Sign-on (SSO) being seamlessly supported across such a broad range of apps, Trustd MTD’s integration with Azure AD for conditional access to company resources means that we can together ensure that company data is inaccessible to compromised users for your business’ key and sensitive apps.
Benedict Jones, Co-Founder, Traced
Free Zero Trust white paper
To learn more about Zero Trust and how Azure AD integrates with Traced’s MTD solution, download the free Trustd whitepaper “Zero Trust mobile security in a perimeter-less world.”
About Traced
Traced’s vision is to make the invisible visible.
It’s about making software that shines a light on threats that are invisible to traditional forms of detection. It’s about making sure their software protects people by being easy to understand, effective, and affordable. And it’s about respecting users’ and employees’ privacy by being transparent about what you’re doing and why.
And it’s about making a different kind of security company. A company that understands and talks about the threats that businesses really face every day, rather than the ones that get the best headlines or induce the greatest fear. For more information, visit the Traced website.
Learn more
- Embrace proactive security with Zero Trust.
- Assess your organization’s Zero Trust maturity.
- Learn about identity and access solutions from Microsoft.
To learn more about the Microsoft Intelligent Security Association (MISA), visit the website where you can learn about the MISA program, product integrations, and find MISA members. Visit the video playlist to learn about the strength of member integrations with Microsoft products.
To learn more about Microsoft Security solutions, visit our website. Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
The post Implementing Zero Trust access to business data on BYOD with Trustd MTD and Microsoft Entra appeared first on Microsoft Security Blog.
Source: Microsoft Security
